Confidential Computing Unveiling a New Era in Security
Confidential Computing sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. This innovative approach to data protection ensures that sensitive information remains secure, even when processed in untrusted environments, revolutionizing the landscape of cybersecurity.
At its core, Confidential Computing introduces a paradigm shift by utilizing specialized hardware, such as Trusted Execution Environments (TEEs), to create secure enclaves for data processing. Unlike traditional computing methods, which often expose data to potential threats during processing, this technology encapsulates data in a secure environment, significantly reducing the risk of unauthorized access. Real-world applications span diverse industries, from healthcare to finance, showcasing its ability to maintain the integrity and confidentiality of sensitive information while enabling organizations to leverage cloud computing capabilities.
Understanding the concept of Confidential Computing is essential for grasping its significance in cybersecurity.
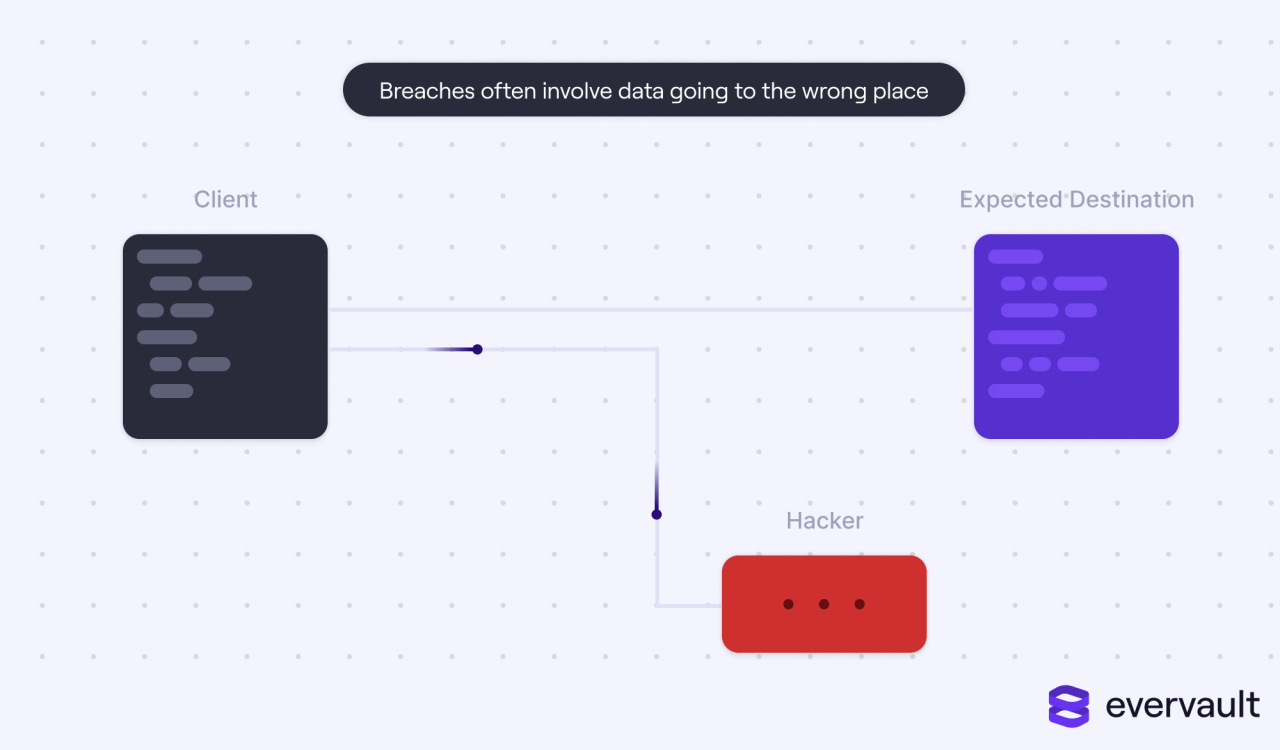
Confidential Computing represents a transformative approach to data protection in the digital age, addressing the growing concerns surrounding data privacy and security. As organizations increasingly rely on cloud services and third-party applications, the challenges of protecting sensitive data in use have escalated. Confidential Computing provides a robust framework to safeguard this data while it is processed, thereby elevating the standards of cybersecurity.The foundational principles of Confidential Computing rest on the concept of hardware-based Trusted Execution Environments (TEEs).
TEEs create isolated execution environments within a computing system where sensitive data can be processed securely, without exposure to the host operating system or any unauthorized users. This isolation is critical, as traditional computing paradigms often expose data to potential risks during its processing stage. In addition to ensuring data confidentiality, TEEs also guarantee data integrity and authenticity, enabling secure computations even in untrusted environments.
Distinguishing Factors from Traditional Computing Paradigms
Confidential Computing diverges significantly from traditional computing paradigms in several ways. Traditional computing typically relies on software-based security measures, which can be vulnerable to various attacks, such as malware or insider threats. By contrast, Confidential Computing leverages hardware-based security features that provide a higher level of assurance against these threats. The key differences include:
- Data Protection During Processing: Unlike traditional methods where data is only secured at rest or in transit, Confidential Computing ensures that data remains protected even while it is being processed.
- Isolation of Sensitive Data: TEEs isolate sensitive workloads, preventing unauthorized access from the host environment and other processes, which is a limitation in traditional computing.
- Enhanced Trust: The use of hardware-based security mechanisms fosters greater trust among users and organizations, as they can verify that their data remains confidential and untampered with during computation.
Real-world applications of Confidential Computing span various industries, highlighting its versatility and effectiveness. Financial institutions utilize this technology to secure sensitive transaction data during processing, ensuring compliance with regulatory requirements. Healthcare organizations deploy Confidential Computing to protect patient records and sensitive health data while enabling collaborative research across institutions without compromising privacy. Additionally, cloud service providers integrate Confidential Computing to offer secure environments for client applications, ensuring that even the service provider cannot access the underlying sensitive data.
The emergence of Confidential Computing not only addresses contemporary cybersecurity challenges but also empowers organizations to innovate securely, fostering a trusted digital ecosystem.
The architecture of Confidential Computing plays a pivotal role in its effectiveness.
The architecture of Confidential Computing is fundamental to ensuring the confidentiality and integrity of sensitive data during processing. By isolating workloads from the host environment, this architecture provides a robust framework that enables organizations to leverage cloud services while maintaining stringent security requirements.The architecture of Confidential Computing consists of several essential components, each designed to contribute to a secure and efficient processing environment.
These components work together to create a secure enclave that protects data from unauthorized access, even when it is being processed. The key components include the Trusted Execution Environment (TEE), hardware security modules, the hypervisor, and application integration frameworks.
Components of Confidential Computing Architecture
Understanding the individual components of the Confidential Computing architecture is crucial to grasping how they enhance overall security. The following are the primary components and their roles:
- Trusted Execution Environment (TEE): The TEE is a secure area within the main processor that ensures that sensitive data is processed in an isolated environment. It guarantees that the execution of code and access to data remain confidential and protected from external interference.
- Hardware Security Modules (HSMs): HSMs provide physical and logical protection for cryptographic keys used in data encryption and decryption. They ensure that keys are generated, stored, and managed securely, preventing unauthorized access.
- Hypervisor: The hypervisor acts as a control layer that manages virtual machines (VMs) and their interactions with the hardware. In the context of Confidential Computing, it ensures that the VMs operate in isolated sandboxes, protecting the TEE from malicious activities originating from other VMs.
- Application Integration Frameworks: These frameworks facilitate the integration of applications with Confidential Computing services. They help developers easily implement security measures within their applications, ensuring that sensitive data is handled in accordance with compliance requirements.
The interaction between these components significantly enhances security in Confidential Computing. For instance, the TEE relies on the underlying hardware to enforce access controls, while the hypervisor manages VM isolation, effectively creating barriers against potential threats. Additionally, HSMs bolster the encryption mechanisms employed within the TEE, providing a layered security approach that is vital for protecting sensitive workloads.To illustrate the architecture and its functions, a diagram can be visualized as follows:
- At the center, the Trusted Execution Environment (TEE) is depicted, representing the core of secure processing.
- Surrounding the TEE, the Hardware Security Modules (HSMs) are shown, indicating their role in key management.
- On the periphery, the Hypervisor is illustrated, controlling the environment in which the VMs operate to maintain isolation.
- Application Integration Frameworks are positioned alongside the TEE, demonstrating their function in linking applications to the secure environment.
This diagram emphasizes the collaborative nature of each component in creating a secure ecosystem for processing sensitive data, highlighting the critical role that architecture plays in Confidential Computing’s effectiveness.
Confidential Computing employs various technologies to ensure data privacy and security.
Confidential Computing leverages cutting-edge technologies to protect sensitive data during processing, ensuring a secure and private environment. This section delves into the primary technologies utilized within Confidential Computing, highlighting their advantages, disadvantages, and real-world applications.
Trusted Execution Environments (TEEs)
Trusted Execution Environments (TEEs) are secure areas within a processor that allow code and data to be protected from outside access or interference, even if the main operating system is compromised. They are crucial in safeguarding sensitive transactions and are utilized in various applications, including financial transactions and personal data protection.The advantages and disadvantages of TEEs are as follows:
Advantages
TEEs provide strong isolation from other software running on the device, ensuring that sensitive data is not exposed to potentially malicious applications.
They facilitate secure computation without revealing the underlying data, which is essential for various applications like cloud computing, where data privacy is paramount.
Disadvantages
The implementation of TEEs can be complex and may require specific hardware support, which limits their adoption across different platforms.
There is potential for side-channel attacks, which can exploit the physical implementation of the TEE to extract sensitive information.
Case studies have illustrated the successful use of TEEs in various sectors. For instance, in the financial services industry, companies have utilized TEEs to ensure secure transactions and protect user credentials, significantly reducing the risk of data breaches. In healthcare, TEEs have been employed to manage sensitive patient data securely, allowing for data sharing while maintaining patient confidentiality.
Homomorphic Encryption
Homomorphic encryption is a method that allows computations to be performed on encrypted data without the need to decrypt it first. This technology is pivotal for situations where data privacy needs to be maintained while still allowing for analysis and processing.The advantages and disadvantages of homomorphic encryption include:
Advantages
Data remains encrypted during processing, significantly enhancing security and privacy.
It enables secure outsourcing of computation to cloud services without exposing sensitive information. –
Disadvantages
The computational overhead associated with homomorphic encryption can be considerable, leading to slower processing speeds compared to traditional methods.
Implementation can be complex, requiring specialized knowledge, which may deter some organizations from adopting this technology.
One notable case where homomorphic encryption has been effectively implemented is in the field of data analytics for healthcare research. Researchers can analyze patient data for trends without ever accessing the actual data itself, thereby ensuring compliance with stringent privacy regulations.
Secure Multi-Party Computation (SMPC)
Secure Multi-Party Computation allows multiple parties to jointly compute a function over their inputs while keeping those inputs private. This technology is particularly useful in scenarios where collaboration is necessary, but data privacy is a concern.The advantages and disadvantages of SMPC are:
Advantages
SMPC facilitates collaborative data analysis without compromising the confidentiality of individual inputs.
It promotes trust among parties, as no single party has access to all the data. –
Disadvantages
The complexity of the protocols involved may lead to increased computational costs and resource requirements.
Latency can be an issue in real-time applications due to the need for multiple rounds of communication among parties.
An example of SMPC in action is in financial audits, where multiple institutions can validate transactions without revealing their sensitive data. This has enhanced transparency in financial systems while protecting proprietary information.
Encryption at Rest and in Transit
Encryption at rest and in transit ensures data security when stored and while being transmitted. This dual-layered encryption strategy is essential for protecting sensitive information across various systems.The advantages and disadvantages of these encryption methods include:
Advantages
They protect data from unauthorized access, ensuring that information remains confidential regardless of its state.
Compliance with regulatory requirements is facilitated, as many regulations mandate the protection of sensitive data. –
Disadvantages
Management of encryption keys can become complex and must be handled carefully to prevent unauthorized access.
Performance overhead may occur, particularly in systems with large volumes of data, affecting speed and efficiency.
A concrete example of encryption at rest and in transit can be observed in cloud service providers, which implement these measures to protect client data, thus enhancing trust and security in cloud environments.
Application of Privacy-Preserving Technologies in Real-World Scenarios
The application of these technologies has been transformative across various industries. For instance, in the retail sector, companies have utilized encryption and TEEs to protect customer information during transactions, thereby enhancing consumer confidence and loyalty. In the supply chain management realm, the use of SMPC has fostered collaboration among suppliers while maintaining the confidentiality of proprietary data. These implementations showcase the potential of Confidential Computing technologies to create secure and private computing environments, essential in today’s data-driven world.
The impact of Confidential Computing on cloud services is transformative and crucial for enterprises.

The emergence of Confidential Computing represents a pivotal shift in the landscape of cloud services, offering enterprises enhanced security and trust. As organizations increasingly move sensitive workloads to the cloud, the need for robust protection mechanisms has never been more critical. This technology enables data to be processed in a secure environment, protecting it from unauthorized access even during computation.Confidential Computing redefines cloud computing dynamics by establishing a secure enclave for sensitive data.
This creates a layer of protection that is distinct from traditional security measures. The secure enclaves protect data in use, ensuring that it remains confidential and isolated from other processes and users within the cloud environment. Such capabilities significantly reduce the risk of data breaches and position enterprises to conduct business with greater confidence.
Comparison of Traditional Cloud Security Measures and Confidential Computing
Traditional cloud security measures primarily focus on protecting data at rest and in transit. These measures include encryption, firewalls, and access controls, which, while essential, often leave data vulnerable during computation. In contrast, Confidential Computing employs hardware-based security features to secure data while it is being processed. This advancement leads to a fundamental shift in how organizations think about data protection.The differences between traditional cloud security and Confidential Computing can be summarized as follows:
- Data Protection During Computation: Traditional methods do not secure data in use, whereas Confidential Computing ensures that sensitive data remains encrypted even during processing.
- Isolation of Sensitive Workloads: Confidential Computing allows for the isolation of workloads within secure enclaves, reducing exposure risks from other processes in the cloud.
- Enhanced Compliance and Trust: Organizations can comply with stringent regulatory requirements more easily, as Confidential Computing provides verifiable proof that sensitive data is handled securely.
- Protection Against Insider Threats: With traditional security measures, insiders can potentially access sensitive data. Confidential Computing minimizes this risk by restricting access to data within secure environments.
The adoption of Confidential Computing offers several distinct benefits for organizations:
- Increased Security Posture: By reducing the attack surface, enterprises can significantly enhance their overall security posture, making it more difficult for adversaries to exploit vulnerabilities.
- Facilitating Data Collaboration: Organizations can securely share and analyze sensitive information without exposing the underlying data, leading to improved collaboration and innovation.
- Optimizing Cloud Utilization: Businesses can confidently move more workloads to the cloud, maximizing the benefits of cloud scalability and efficiency while maintaining data confidentiality.
- Streamlined Compliance Processes: With robust security assurances, businesses can more easily navigate compliance frameworks, reducing the complexity of adhering to regulations.
By addressing the inherent limitations of traditional security measures, Confidential Computing enhances the viability of cloud services for enterprises, fostering an environment where sensitive data can be processed securely and efficiently, thereby transforming cloud computing into a more trusted platform.
Regulatory compliance challenges in the context of Confidential Computing require careful consideration.
The integration of Confidential Computing into organizational practices brings forth a myriad of regulatory compliance challenges that must be navigated with diligence. As organizations adopt this advanced technology, they face scrutiny from various regulatory bodies that impose strict data protection standards tailored to different industries. Understanding these regulations is paramount for ensuring that Confidential Computing can be leveraged effectively without compromising compliance.Implementing Confidential Computing requires a nuanced understanding of the regulatory landscape.
Different industries are subject to specific data protection regulations that can influence how this technology is adopted. The challenge lies in aligning the capabilities of Confidential Computing—such as data encryption and secure enclave technology—with the multifaceted requirements of these regulations. Organizations must proactively identify and address compliance obligations while harnessing the benefits of this transformative technology.
Key Regulations Impacting Confidential Computing
An understanding of key regulations is essential for organizations seeking to implement Confidential Computing. Below is a summary of notable regulations and their implications for data protection:
| Regulation | Industry | Implications for Data Protection |
|---|---|---|
| General Data Protection Regulation (GDPR) | All industries operating in the EU | Requires stringent data handling processes, including encryption and data minimization, which align with Confidential Computing’s capabilities. |
| Health Insurance Portability and Accountability Act (HIPAA) | Healthcare | Mandates the protection of patient information; Confidential Computing can enhance data security measures for sensitive health data. |
| Payment Card Industry Data Security Standard (PCI DSS) | Financial Services/Retail | Sets security standards for processing card payments; Confidential Computing can provide additional security layers for transaction data. |
| Federal Information Security Management Act (FISMA) | U.S. Federal Agencies | Establishes a framework for securing government information systems, which can benefit from the secure processing capabilities of Confidential Computing. |
| California Consumer Privacy Act (CCPA) | Businesses operating in California | Imposes requirements on data collection and user consent; Confidential Computing can help manage consumer data in compliance with privacy rights. |
To ensure compliance while utilizing Confidential Computing, organizations can adopt several strategies. These include conducting comprehensive risk assessments to identify compliance gaps, investing in training for personnel on regulatory requirements, and establishing robust governance frameworks that incorporate privacy-by-design principles. Furthermore, collaboration with legal and compliance experts can guide organizations through the complexities of regulatory landscapes and facilitate a smoother integration of Confidential Computing into existing workflows.
“Compliance is not the end goal; it is the foundation for building trust with customers while leveraging innovative technologies like Confidential Computing.”
Confidential Computing has significant implications for data sharing between organizations.
In an increasingly interconnected world, organizations often need to share sensitive data to collaborate effectively. However, traditional methods for data sharing can expose this information to risks such as unauthorized access and data breaches. Confidential Computing addresses these challenges by providing a secure environment for data to be processed and shared while maintaining privacy and confidentiality.Secure data sharing is fraught with challenges, primarily due to the risks associated with data exposure during transit and processing.
Confidential Computing utilizes hardware-based Trusted Execution Environments (TEEs), which isolate sensitive data and applications from the rest of the system. This technology ensures that even if the system itself is compromised, the data remains protected within the secure enclave. Through this approach, organizations can exchange information without fear of interception or misuse.
Process of Secure Data Sharing
The process of secure data sharing enabled by Confidential Computing can be illustrated through a practical example involving healthcare organizations sharing patient data for research purposes. Here’s how the process unfolds:
1. Data Encryption
Before sharing, the data is encrypted at the source organization. This ensures that only authorized entities can access the information.
2. Use of Trusted Execution Environments
The healthcare organization utilizes TEEs to create a secure enclave where data can be processed without exposing it to the broader system. This means that sensitive patient data remains encrypted and secure during analysis.
3. Collaboration with Third Parties
Researchers from partner organizations can access the TEE to run their algorithms on the encrypted data. This allows them to derive insights without ever seeing the actual patient information.
4. Results Extraction
After processing, the results—stripped of any personally identifiable information—are collected from the secure enclave and shared with the collaborating organizations.This secure method allows organizations to collaborate on critical projects while adhering to strict data protection regulations, such as HIPAA or GDPR.
Benefits of Enhanced Collaboration
The adoption of Confidential Computing can significantly enhance collaboration across organizations. The benefits include:
Improved Trust
Organizations are more likely to share data when they trust that their sensitive information is protected against breaches.
Regulatory Compliance
With built-in security measures, organizations can meet legal requirements for data protection, facilitating smoother collaborations across jurisdictions.
Accelerated Innovation
Access to shared data enables organizations to develop new products and services more rapidly, fostering innovation in various sectors like healthcare, finance, and technology.
Cost Efficiency
By minimizing the risks associated with data sharing, organizations can reduce the costs related to data breaches and compliance fines, resulting in overall savings.
Confidential Computing empowers organizations to collaborate securely and innovate without compromising sensitive information.
Evaluating the performance of Confidential Computing solutions is necessary for informed decision-making.
Evaluating the performance of Confidential Computing solutions is crucial for organizations seeking to enhance data security while maintaining operational efficiency. As businesses increasingly adopt these technologies to protect sensitive information in multi-cloud environments, understanding the performance metrics can drive more informed decisions in technology selection and implementation.Performance assessment of Confidential Computing technologies often involves several key metrics. These metrics help organizations measure the effectiveness, efficiency, and overall impact of the solutions on their operations.
Typical metrics include throughput, latency, resource utilization, and the cost-effectiveness of deploying these technologies in various environments.
Key Performance Metrics
The evaluation of Confidential Computing solutions hinges on specific performance metrics that provide insights into their capabilities. Understanding these metrics is essential for organizations to gauge their effectiveness. The following key metrics are commonly used:
- Throughput: This metric indicates the amount of data processed in a given timeframe and is vital for assessing the scalability of a Confidential Computing solution. Higher throughput generally signifies better performance, especially for data-intensive applications.
- Latency: Latency measures the delay between a request and the response, which is critical in real-time applications. Low latency is indicative of efficient processing, enabling faster decision-making in sensitive environments.
- Resource Utilization: This evaluates how effectively the underlying resources (CPU, memory, and storage) are used during operation. Efficient resource utilization can lead to reduced costs and improved performance.
- Cost-Effectiveness: Analyzing the total cost of ownership, including deployment, maintenance, and operational costs, provides insights into the economic viability of the solutions being evaluated.
Comparative Analysis of Market Solutions
A comparative analysis of the leading Confidential Computing solutions on the market reveals distinct features and performance levels among the providers. Some notable solutions include:
| Solution | Provider | Key Features | Performance Rating |
|---|---|---|---|
| AWS Nitro Enclaves | Amazon Web Services | Integration with AWS services, scalability, and strong security | High throughputs with low latency |
| Microsoft Azure Confidential Computing | Microsoft | Integration with Azure services, robust compliance, and strong encryption | Moderate latency with high security |
| Google Cloud Confidential Computing | Google Cloud | Open-source tools, strong isolation mechanisms, and scalability | High performance with efficient resource utilization |
This comparative analysis highlights how different providers tailor their offerings to meet various organizational needs. Companies can leverage this information to select the solution that aligns best with their operational requirements and performance expectations.
User Experiences and Performance Benchmarks
User experiences and performance benchmarks provide valuable insights into the real-world applications of Confidential Computing technologies. Organizations utilizing these solutions often cite enhanced security and compliance as significant benefits. For instance, benchmarking studies have shown that AWS Nitro Enclaves can deliver up to 99% higher throughput compared to traditional environments. Users report lower operational costs due to reduced resource consumption, facilitating better budget management.Furthermore, organizations have shared their experiences with latency and operational impact.
Many users of Microsoft Azure Confidential Computing have noted that while there may be slight increases in latency due to added security layers, the trade-off is well justified by the enhanced protection of sensitive data. In summary, evaluating the performance of Confidential Computing solutions involves a detailed analysis of critical metrics, comparative insights into market offerings, and user feedback that underscores their effectiveness in real-world scenarios.
This comprehensive approach ensures that organizations can make informed decisions that align with their security and operational needs.
The future of Confidential Computing is promising, with ongoing advancements and innovations.
The landscape of Confidential Computing is rapidly evolving, characterized by notable advancements and innovations that promise to redefine data security and privacy in the coming years. As organizations increasingly recognize the importance of protecting sensitive information, the drive towards adopting Confidential Computing technologies is gaining momentum. This section explores emerging trends and technologies poised to shape the future of this field, while also addressing potential challenges that may hinder its widespread acceptance.
Emerging Trends and Technologies
Several trends are emerging within the realm of Confidential Computing that signify a transformative shift in how sensitive data is managed and processed. These trends highlight the technological advancements that are set to enhance the capabilities of Confidential Computing.
- Integration with Cloud Services: As more businesses migrate to cloud environments, the integration of Confidential Computing with cloud services is becoming essential. Major cloud providers are beginning to offer Confidential Computing solutions, enabling organizations to process sensitive data securely without exposing it to unauthorized access.
- Advancements in Hardware Security: Innovations in hardware security technologies, such as Trusted Execution Environments (TEEs) and Secure Enclaves, are paving the way for more robust Confidential Computing solutions. These hardware-based security measures provide isolated environments for processing sensitive workloads, further enhancing data protection.
- Regulatory Compliance and Standards: The establishment of regulatory frameworks and standards focused on data protection is driving the adoption of Confidential Computing. Compliance with laws such as the General Data Protection Regulation (GDPR) necessitates enhanced security measures, positioning Confidential Computing as a strategic solution.
Potential Challenges to Adoption
While the prospects for Confidential Computing are promising, several challenges may impede its widespread adoption. Understanding these obstacles is crucial for stakeholders aiming to leverage this technology effectively.
- Complexity of Implementation: The integration of Confidential Computing solutions requires significant technical expertise and resources. Organizations may face challenges in deploying and managing these systems, particularly if they lack the necessary skills.
- Performance Overheads: The additional security layers introduced by Confidential Computing can lead to performance overheads, impacting processing speeds. Balancing security and performance remains a critical consideration for organizations adopting this technology.
- Cost Implications: Implementing Confidential Computing solutions can be expensive, particularly for smaller organizations. The costs associated with acquiring specialized hardware and software may deter potential adopters.
Speculative Analysis of Future Evolution
The next decade is likely to witness significant evolution in Confidential Computing, driven by both technological advancements and changing organizational needs. As this technology matures, several predictions can be made about its trajectory.
- Enhanced Interoperability: Future developments will likely focus on enhancing interoperability between different Confidential Computing platforms, enabling seamless data sharing and processing across diverse environments.
- Broader Adoption Across Industries: As industries increasingly recognize the value of data security, sectors such as finance, healthcare, and government are expected to adopt Confidential Computing more widely, driven by the need to protect sensitive information.
- Increased Collaboration: Collaborations among tech companies, research institutions, and regulatory bodies will be pivotal in advancing Confidential Computing. These partnerships can foster innovation and establish best practices, further promoting the technology’s adoption.
- Integration of AI and Machine Learning: The convergence of Confidential Computing with artificial intelligence (AI) and machine learning (ML) will yield new opportunities for secure data processing and analysis. This integration can enable organizations to derive insights from sensitive data while maintaining confidentiality.
As the landscape of data security continues to evolve, Confidential Computing stands at the forefront, poised to revolutionize the way organizations handle sensitive information.
Real-world case studies of organizations utilizing Confidential Computing can provide valuable insights.
Confidential Computing has emerged as a transformative technology, allowing organizations to secure sensitive data during processing. This advancement not only protects information but also fosters trust among stakeholders. By examining real-world case studies, we can glean valuable lessons and best practices, as well as understand the challenges organizations have faced during implementation.In the realm of Confidential Computing, various organizations have embarked on initiatives to safeguard their data while maintaining operational efficiency.
These case studies not only highlight successful implementations but also provide a roadmap for others considering similar solutions.
Case Study: IBM and the Financial Services Industry
IBM has been at the forefront of implementing Confidential Computing solutions in the financial services sector. The company developed a data encryption platform that ensures sensitive financial transactions remain secure. This case demonstrates the importance of protecting data integrity and confidentiality in a highly regulated environment.The following key insights were derived from IBM’s implementation:
Data privacy is paramount, particularly in finance.
Organizations must prioritize encryption and control access to sensitive data.
Collaboration with regulatory bodies enhances trust.
Working closely with regulators ensures compliance and fosters industry-wide confidence.
Education and training are essential.
Staff must be well-versed in confidentiality protocols and the significance of data protection.
The challenges IBM faced included integrating existing legacy systems with new Confidential Computing technologies. This was addressed through phased implementation, allowing for gradual testing and integration without disrupting ongoing operations.
Case Study: Microsoft Azure Confidential Computing
Microsoft has utilized its Azure platform to offer Confidential Computing services that cater to various industries, including healthcare and government. By leveraging hardware-based security enclaves, Azure enables organizations to process sensitive data without exposing it to the host environment.Prominent insights from Microsoft’s initiative include:
Flexibility is key in cloud solutions.
Azure’s adaptability allows organizations to choose the level of security that best meets their needs.
Partnerships enhance capabilities.
Collaborating with third-party vendors can broaden the range of services offered.
Continuous improvement is vital.
Regular updates and improvements to security protocols ensure that the platform remains secure against evolving threats.
Microsoft encountered challenges such as ensuring that hardware security modules (HSMs) were universally compatible. This was overcome by investing in partnerships with hardware manufacturers to ensure consistent quality and performance across devices.
Case Study: Google Cloud Platform’s Confidential VMs
Google has introduced Confidential Virtual Machines (VMs) as part of its cloud offerings. These VMs allow organizations to encrypt data while it is in use, providing an additional layer of security that is particularly relevant in industries dealing with personal information.Key takeaways from Google’s implementation include:
Simplicity in deployment encourages adoption.
A straightforward implementation process increases user engagement and adoption rates.
Transparency builds trust.
Providing clients with clear visibility into security measures fosters confidence in cloud solutions.
Customer feedback drives enhancements.
Regularly soliciting input from users leads to continuous improvement of services.
Google faced obstacles related to customer awareness of Confidential Computing’s capabilities. This was addressed through comprehensive educational campaigns, illustrating how Confidential VMs could meet their specific security needs.These case studies illustrate that while the journey towards implementing Confidential Computing can pose challenges, the benefits far outweigh the hurdles when managed effectively. Organizations can significantly enhance their data security frameworks by adopting best practices and learning from the experiences of industry leaders.
Expert Answers
What is the primary benefit of Confidential Computing?
The primary benefit of Confidential Computing is that it protects data while it is being processed, ensuring that sensitive information remains secure from unauthorized access, even in untrusted environments.
How does Confidential Computing differ from traditional encryption?
While traditional encryption secures data at rest or in transit, Confidential Computing secures data during processing, offering an added layer of protection where vulnerabilities are most prevalent.
Can Confidential Computing be used in all cloud environments?
Yes, Confidential Computing can be implemented in various cloud environments, but its effectiveness may depend on the specific architecture and support for TEEs provided by the cloud service provider.
What industries can benefit from Confidential Computing?
Industries such as finance, healthcare, and data analytics can greatly benefit from Confidential Computing, as these sectors often handle sensitive information that requires stringent security measures.
Is Confidential Computing compliant with data protection regulations?
Confidential Computing can assist organizations in meeting data protection regulations by securing sensitive data during processing; however, compliance will still depend on how organizations implement the technology and adhere to specific regulatory requirements.

Rahmi Miller is a passionate technology writer at bulldogrool.com, specializing in emerging digital trends, smart innovations, and practical tech solutions for everyday life. With a keen eye for detail and a deep curiosity about how technology shapes the future, Rahmi delivers clear, engaging, and insightful content that helps readers stay ahead in a fast-moving digital world.








